Look a like phishing attacks, also known as “typosquatting” have been steadily increasing for the past several years. They have sharply increased during the COVID-19 Pandemic. Over 75% of the attacks are spear phishing attacks to harvest logins and credentials.
A common way for criminals to get your login credentials or other sensitive information is to simply ask for it. This may seem hard to believe at first, but the criminals will copy the look and feel of the real website to create their own fake site. The attackers create a website or email address that is similar to a legitimate one, but with slight variations such as a different spelling in the domain name. Can you tell the difference between these two Microsoft 365 login screens:
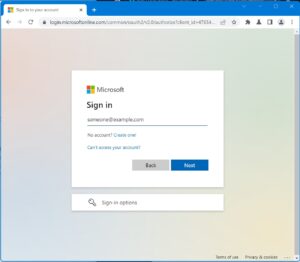
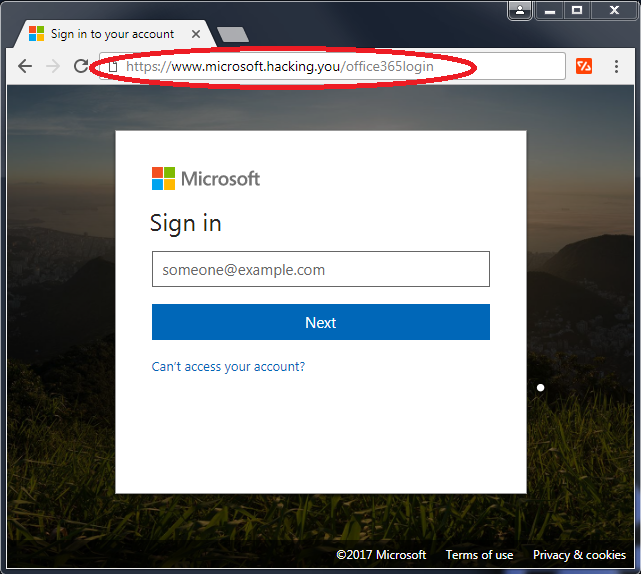
The first picture is the real Microsoft Office 365 login screen; the second one has fake URL (circled in red). Another example is instead of “amazon.com” the attacker may use “amazzon.com” or “amaz0n.com”. These small differences can be hard for users to spot. Your staff will then enter their login credentials on the fake website, which can then be used by the attacker for fraudulent activities.
Look a like phishing can also be done on social media platforms as well by creating fake accounts that mimic the real one. The attackers often use slight variations in the name or handle. The attacker will then send requests to the victim’s friends or followers, asking them to click on a phishing or malware link.
Like all skills, spotting fake login pages and links takes practice. One of the best ways to train your staff and to test their knowledge is with cyber security phishing training. Look a like phishing attacks give a fast path for the criminals to gather your staff’s login information.
To learn more, book a Free IT consultation with us to review your staff’s phishing training program and awareness.






